| weo | Date: Sunday, 2012-01-15, 11:29 AM | Message # 1 |
|
Colonel
Group: Moderators
Messages: 151
Status: Offline
| Network Administration - pfSense is an open source application routing functionality into strong and free firewall, this application will allow you to extend your network without compromising security. With many of its advantages should be popular everywhere, from homes to businesses. In the following article we will guide you to configuring a pfSense 2.0 Cluster Failover using CARP.
System Requirements
To make this process we need two identical computers, with a minimum of 3 network card and a subnet for synchronization of network traffic (network traffic).
For example IP address will be used in the article:
Network Configuration:
Firewall 1
WAN IP: 192.168.100.1
SYNC IP: 10.155.0.1
LAN IP: 192.168.1.252 Firewall 2
WAN IP: 192.168.100.2
SYNC IP: 10.155.0.2
LAN IP: 192.168.1.253
The two IP addresses below to share between the firewall:
Virtual WAN IP: 192168100200
Virtual LAN IP: 192.168.1.254
This guide assumes you have installed pfSense on both computer and network card configured with IP address ... and users each have experience working with pfSense (mainly around the web management interface).
For example illustrates the model that we built:
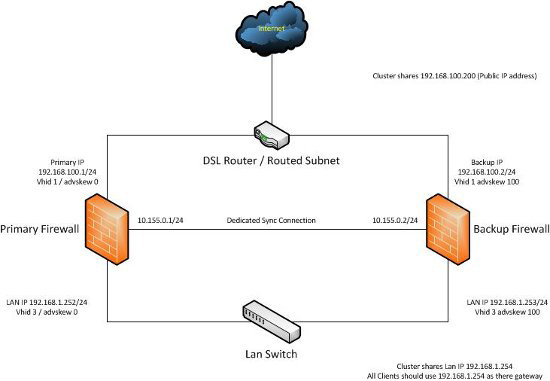
Construction Cluster
First you need to configure a firewall rule on both boxes box to allow the firewall to communicate with each other on the SYNC card.
To do this, click on "Firewall | Rules", select SYNC Interface Section. Click the Plus button to add a new firewall rule. Set the "Protocol" to "any", add a description to identify rules. Click Save, then click Apply Changes, if necessary.
Still on the backup firewall, here we need to configure synchronization profiles for CARP and it's just a copy. Click "Firewall | Vitrual IPs"> "Firewall | Vitrual IPs", check the box "Synchronize Enabled". Select "Synchronize Interface to SYNC", then save the changes.
Complete backup firewall configuration, we now proceed to configure the synchronization of CARP on firewalls.
Log into your main firewall, click on "Firewall | Virtual IPs", switch to tab "CARP Settings" and check the box "Synchronize Enabled". In Section Synchronize Interface select "SYNC" as the default, check the box marked under "Synchronize Rules", "Synchronize NAT", "Synchronize Virtual IPs".
Then enter the IP address of the copy SYNC firewall box "Synchronize to IP" and set the password in the box "Remote System Password".
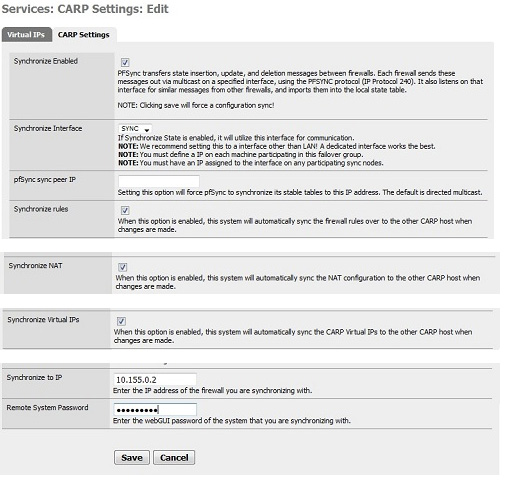
Click Save to save your changes.
Next we configure the Virtual IP address for both firewalls to be used. To do this go to "Firewall | Virtual IPs" and switch to tab "Virtual IPs".
First set the IP address for WAN Interface section, click the Plus button to add the virtual IP, make sure that the IP model is set at CARP. WAN address will be used throughout your system regardless of the firewall is enabled or copy.
Next create a password in the "Virtual IP Password", to maintain a value of "VHID Group" and the value of 0 for "Advertising Frequency," a little more description in Description and click Save to save it.
Similarly, we configure Virtual IP address for the LAN Interface section. The steps none other than the instructions on to the WAN, private parts "VHID Group" you change the value is 3, put a different description and click Save to save your changes.
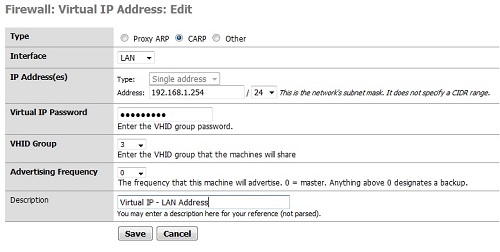
And now you can see in the section "Firewall | Virtual IPs" appears in the list are two types of CARP virtual IPs.
If you log into web interface of the firewall back up and click on "Firewall | Virtual IPs," you will see the virtual IPs sync with backup firewall.
Now is the time to see how it works. Two pfSense firewall will continuously synchronize their rules, NAT, virtual IPS and any other settings you selected in the Synchronize option. For that reason the firewall to be decommissioned, a copy of it is continuous.
In test conditions, copies firewall will accept the latency is 10 seconds, by the FreeBSD operating system will apply to the virtual IP address for an interface when disconnected from the main firewall.
Failover Testing
You can test by unplugging the network cable or disable the firewall while the continuous ping to the IP address of the LAN or WAN. You will see the IP reduced to a few seconds in the other firewall.
|
| |
|
|